What is Pentesting?
How Does It Work Step-by-Step?

May 16, 2023
Estimated Reading Time: 3 minutes
Introduction
Penetration testing, commonly referred to as pentesting, is an ethical hacking practice employed to assess the security posture of computer systems, networks, and applications. Unlike malicious hacking, which seeks to exploit vulnerabilities for malicious intent, pentesting is conducted by skilled professionals to identify weaknesses and provide recommendations for remediation. By simulating real-world attacks, organizations can proactively strengthen their defenses and protect sensitive data from cyber threats.
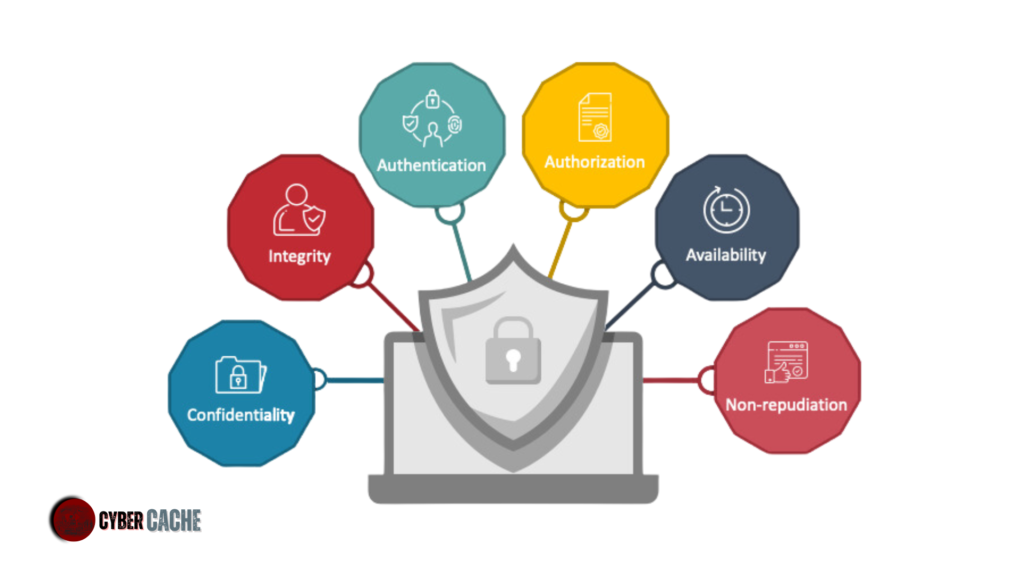
Why Is Pentesting Important?
In the ever-evolving landscape of cyber threats, pentesting plays a pivotal role in an organization’s cybersecurity strategy. The primary reasons why pentesting is crucial include:
Vulnerability Detection: Pentesting allows organizations to uncover security weaknesses before malicious actors exploit them. It provides valuable insights into potential vulnerabilities in software, hardware, and network configurations.
Risk Mitigation: By identifying and mitigating vulnerabilities proactively, pentesting reduces the risk of data breaches, financial losses, and reputational damage caused by successful cyberattacks.
Regulatory Compliance: Many industries have specific compliance requirements for data protection. Pentesting helps organizations meet these regulatory standards and demonstrate their commitment to cybersecurity best practices.
Continuous Improvement: Regular pentesting allows organizations to continuously improve their security measures. It provides valuable feedback that can be used to refine security policies and enhance overall cybersecurity readiness.
Step-by-Step Guide
Step 1: Pre-Engagement Phase The journey begins with clear communication between the organization and the pentesting team. During this phase, the scope and objectives of the assessment are defined, and legal agreements are established. The pentesting team gains a comprehensive understanding of the organization’s infrastructure, assets, and specific goals for the assessment.
Step 2: Information Gathering The pentesting team initiates the reconnaissance phase by collecting information about the organization’s systems, networks, and applications. This involves passive techniques such as open-source intelligence (OSINT) and publicly available information gathering.
Step 3: Threat Modeling and Planning In this critical stage, the pentesting team evaluates the collected information to create a threat model. They identify potential attack vectors, prioritize targets, and devise a detailed plan for the pentesting engagement.
Step 4: Vulnerability Scanning Automated scanning tools are deployed to assess the organization’s systems and networks for known vulnerabilities. This step helps identify low-hanging fruit and guides subsequent manual testing efforts.
Step 5: Manual Testing – Exploitation The heart of pentesting lies in this phase, where skilled ethical hackers manually explore the target systems for security flaws. By employing various attack techniques, they attempt to exploit identified vulnerabilities and gain unauthorized access to systems and sensitive data.
Step 6: Post-Exploitation After successfully compromising systems, the pentesting team investigates the extent of damage that an attacker could cause. This includes assessing data exfiltration, privilege escalation, and lateral movement possibilities within the network.
Step 7: Reporting and Remediation Following the completion of the pentesting engagement, the team compiles a detailed report outlining the findings, potential risks, and recommended remediation strategies. This report equips the organization with actionable insights to prioritize and address security weaknesses effectively.
Conclusion
Penetration testing is a proactive and invaluable tool in an organization’s cybersecurity arsenal. By simulating real-world attacks, pentesting empowers organizations to identify and rectify security weaknesses before they can be exploited by malicious actors. Through meticulous planning, skilled execution, and actionable reporting, pentesting plays a crucial role in safeguarding valuable assets, maintaining customer trust, and fortifying defenses against the ever-evolving landscape of cyber threats. Embracing pentesting as an integral part of a robust cybersecurity strategy empowers organizations to stay one step ahead in the battle against cybercrime.

Discover our comprehensive range of cybersecurity services designed to protect your organization’s digital assets. From threat intelligence and security assessments to cloud pentesting, we provide tailored solutions to ensure your systems and data are secure.
Think
Copyright ©2022 Cyber Cache All Rights Reserved
