Web Application Pentest
Enhancing Your Application's Security
At Cyber Cache we offer a comprehensive Web Application Penetration testing service to ensure the robustness of your web-based applications. Our skilled cybersecurity professionals use cutting-edge techniques to assess your application’s security, identify vulnerabilities, and provide actionable recommendations to fortify your defenses.
What is Web Application Penetration testing?
Web Application Pentesting, also known as Web App Security Testing, is a crucial process of evaluating the security posture of your web applications. Our team conducts simulated attacks on your application to uncover potential vulnerabilities, such as SQL injection, cross-site scripting (XSS), authentication flaws, and more.
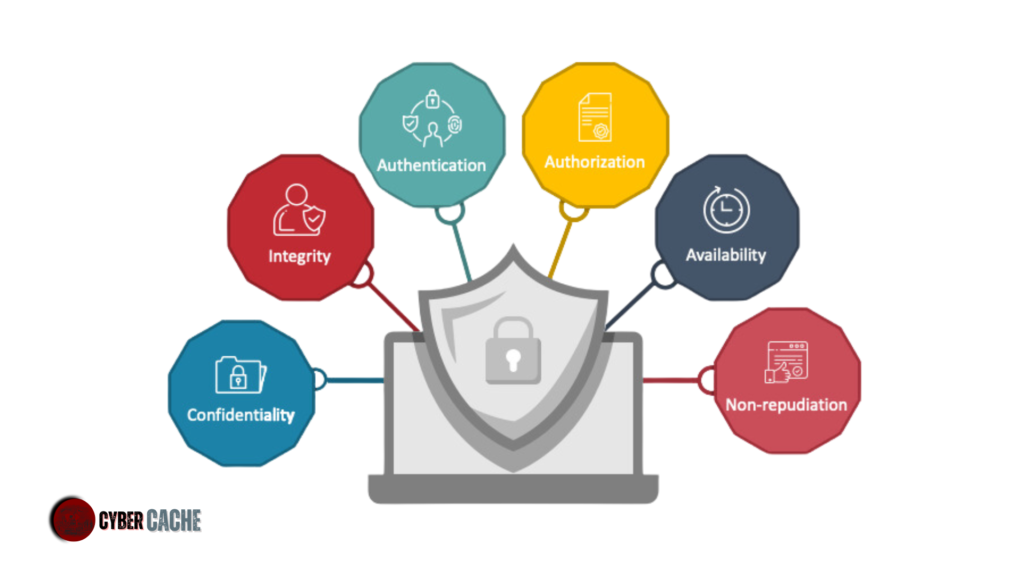
What is the main objective of Web Application Pentesting?
Web Application Pentesting aims to identify vulnerabilities and security weaknesses within web-based applications. By simulating real-world attacks, it helps assess the application’s resilience against potential cyber threats.
What types of vulnerabilities can be discovered during a Web Application Pentest?
Web Application Pentesting can reveal various vulnerabilities, such as SQL injection, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF), insecure authentication mechanisms, session management flaws, and more.

Why should I conduct a Web Application Pentest for my business?
Conducting a Web Application Pentest is essential to proactively identify and address vulnerabilities in your web-based applications. By conducting the test, you can strengthen your application’s security, protect sensitive data, and prevent potential data breaches and cyberattacks.

Why Choose Our Web App Pentest Service?
- Highly Skilled Experts: Our certified cybersecurity professionals have extensive experience in conducting successful Network Pentesting engagements, providing you with accurate and valuable results.
- Comprehensive Assessment: We perform in-depth analysis and testing of your network infrastructure, leaving no stone unturned to identify potential vulnerabilities.
- Actionable Recommendations: After the assessment, we provide a detailed report with clear and actionable recommendations to strengthen your network’s security defenses.
- Proactive Approach: Network Pentesting allows you to stay ahead of cyber threats by identifying and addressing security weaknesses before malicious actors can exploit them.
