Understanding Social Engineering: A Psychological Approach

Estimated Reading Time: 8 minutes
Introduction
In the ever-evolving landscape of cybersecurity, one of the most potent and deceptive threats faced by individuals and organizations alike is social engineering. Unlike traditional hacking techniques that target technical vulnerabilities, social engineering preys on human psychology to manipulate individuals into revealing sensitive information or taking actions that compromise security. In this article, we delve into the fascinating world of social engineering, exploring the psychological tactics used by hackers to exploit human behavior. Understanding these techniques is crucial for enhancing cybersecurity awareness and fortifying ourselves against social engineering attacks.
Understanding Social Engineering: A Psychological Approach
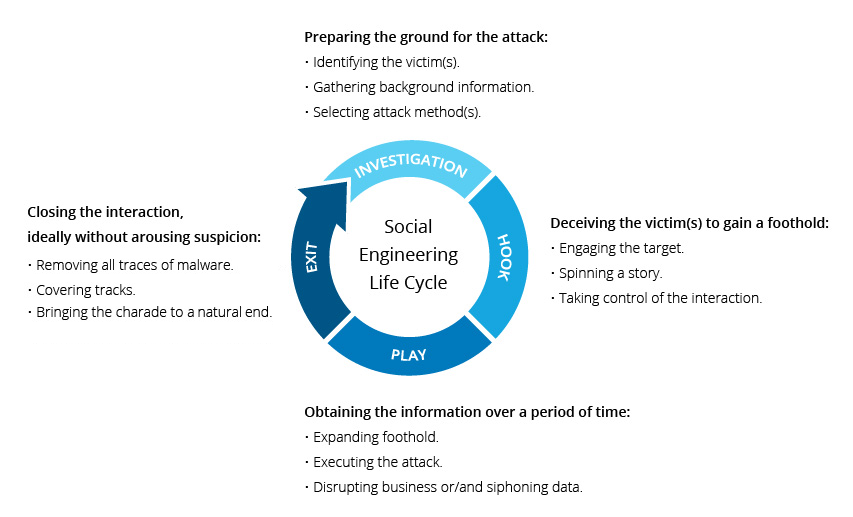
Social engineering exploits the natural human tendency to trust and empathize with others. By understanding human emotions, motivations, and cognitive biases, hackers can craft persuasive narratives that lure victims into unwittingly divulging confidential information, clicking on malicious links, or performing harmful actions. The success of social engineering lies in its ability to bypass technological defenses and directly target the human factor – often considered the weakest link in the cybersecurity chain.
The Power of Persuasion: Techniques Used by Social Engineers
Pretexting: Social engineers create elaborate and convincing scenarios (pretexts) to manipulate targets into divulging information or performing tasks. They might impersonate authority figures, IT personnel, or trusted colleagues to gain the victim’s trust and cooperation.
Phishing: Phishing emails and messages are carefully crafted to evoke urgency, fear, or curiosity, triggering an emotional response that prompts the recipient to take immediate action. By using familiar language and design, hackers deceive users into clicking malicious links or providing login credentials.
Tailgating and Impersonation: In physical social engineering, attackers physically gain access to restricted areas by tailgating behind authorized personnel or impersonating employees or contractors. The human inclination to be helpful can inadvertently lead to unauthorized access.
Baiting: Social engineers use enticing offers, such as free software downloads or USB drives, to tempt victims into taking actions that compromise security. Once the bait is taken, malware is introduced to the victim’s system.
Quid Pro Quo: This technique involves offering something of value in exchange for information or access. For instance, a hacker may pose as technical support, offering to fix a supposed issue in exchange for login credentials.
Cognitive Biases and Vulnerabilities Exploited
Reciprocity: People tend to feel obliged to return favors or help someone who has helped them. Social engineers leverage this bias by offering assistance or incentives to evoke a sense of reciprocity in the target.
Authority Bias: Humans tend to comply with figures of authority or expertise without question. Social engineers exploit this bias by posing as authority figures, making their requests more convincing.
Urgency and Scarcity: A sense of urgency or scarcity can lead individuals to act impulsively without considering potential risks. Social engineers create a sense of urgency to manipulate victims into hasty actions.
Trust and Familiarity: People are more likely to trust and cooperate with those they perceive as familiar or trustworthy. Social engineers capitalize on this by building rapport and trust during interactions.
Curiosity: Humans are naturally curious beings. Hackers exploit this trait by using subject lines or content that pique curiosity, leading victims to click on malicious links or attachments.
Defending Against Social Engineering Attacks
Education and Awareness: Regular cybersecurity training and awareness programs can educate individuals about the various social engineering techniques and red flags to watch for.
Verify Requests: Always verify requests for sensitive information or unusual actions through multiple channels, especially if they come unexpectedly or appear suspicious.
Strong Authentication: Implement multi-factor authentication (MFA) for sensitive accounts to add an extra layer of protection against unauthorized access.
Secure Physical Access: Enforce strict physical security measures to prevent unauthorized individuals from gaining access to restricted areas.
Security Policies and Procedures: Establish clear security policies and procedures that address social engineering threats and ensure employees understand and adhere to them.
Conclusion
Social engineering is a powerful and insidious form of cyber attack that targets the human element in cybersecurity. By exploiting psychological vulnerabilities and cognitive biases, hackers manipulate human behavior to achieve their nefarious goals. Understanding the tactics employed by social engineers is essential for bolstering cybersecurity defenses and creating a vigilant and informed workforce. Through a combination of education, awareness, and robust security measures, we can fortify ourselves against the psychological manipulations of social engineering and build a more resilient digital world. Let us remain vigilant and proactive in the face of this ever-evolving threat to safeguard our digital assets and preserve our cybersecurity.

Discover our comprehensive range of cybersecurity services designed to protect your organization’s digital assets. From threat intelligence and security assessments to cloud pentesting, we provide tailored solutions to ensure your systems and data are secure.
Think
Copyright ©2022 Cyber Cache All Rights Reserved
