What is Cloud Pentesting?
Cloud Pentesting, short for Cloud Penetration Testing, is a proactive security assessment conducted on your cloud-based systems. It involves simulated attacks on your cloud infrastructure to identify weaknesses, misconfigurations, and potential security gaps that could be exploited by malicious actors.
Why is Cloud Pentesting Essential?
As businesses increasingly adopt cloud technologies, it becomes crucial to evaluate the security posture of their cloud environments. Cloud Penetration Testing helps uncover vulnerabilities that could lead to data breaches, unauthorized access, or service disruptions, allowing you to proactively address potential risks.
What Does Our Cloud Pentesting Service Include?
Our Cloud Pentesting service encompasses a comprehensive evaluation of your cloud infrastructure. It includes thorough assessments of cloud providers’ configurations, identity and access management (IAM) policies, data storage security, network security, and more. Our team tests your applications deployed on the cloud, ensuring they adhere to best security practices.
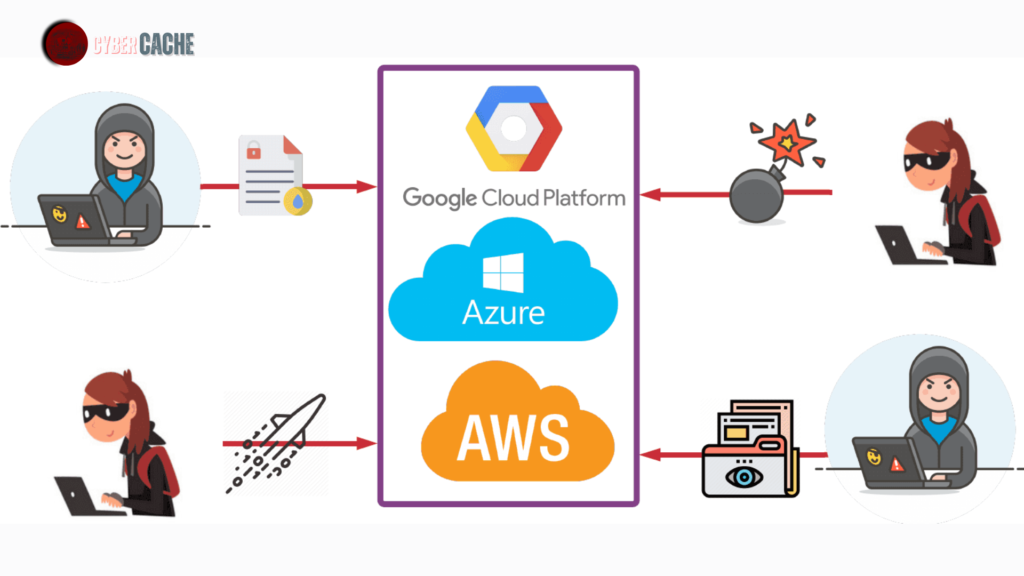
How Do We Approach Cloud Pentesting?
Our team follows a systematic approach to Cloud Pentesting:
- Information Gathering: Understanding your cloud environment, services, and relevant security configurations.
- Threat Modeling: Identifying potential threats and attack vectors.
- Vulnerability Analysis: Scanning for known vulnerabilities and misconfigurations.
- Exploitation: Simulating attacks to validate identified vulnerabilities.
- Reporting: Providing a detailed report with findings, risk ratings, and actionable recommendations.

What Are the Benefits of Our Cloud Pentesting Service?
- Proactively identify and fix security weaknesses before they are exploited.
- Meet compliance requirements and industry standards.
- Safeguard sensitive data stored on the cloud.
- Build trust with customers, partners, and stakeholders by demonstrating a strong security posture.
